How to enable AWS EBS volume encryption by default
Back on May 23rd 2019, AWS announced that all newly created EBS volumes can be encrypted as default. This required the owner/administrator of the AWS account to login and enable this feature. So why is this a good idea? Well a couple reasons:
- With GDPR still very much in the foreground of companies thoughts, making sure all personal data is 100% locked down is of the utmost importance, as is encrypting all data (where possible) in production systems
- In this day and age we as producers of online systems/applications, should be implementing the practice of “Encrypt everything, where possible and feasible”
- Limiting the damage of any potential breach by encrypting the data at rest, means it’s useless to the thief
- If using the AWS managed encryption key, then its free to use. So why wouldn’t you?
How to enable
To enable this feature, login to your AWS account. From the homepage go to services and then EC2. When you are on the EC2 dashboard page, there will be a section on the right of the screen called Account Attributes.
Click on the Settings link and you will be presented with the page in the screenshot below. Check the box next to Encryption. Then you have two options when it comes to the Default encryption key:
- Use the default alias/aws/ebs supplied and maintained by AWS on your behalf, or
- Choose a Customer Master Key (CMK) that you have created in KMS. It will be your responsibility to maintain this key
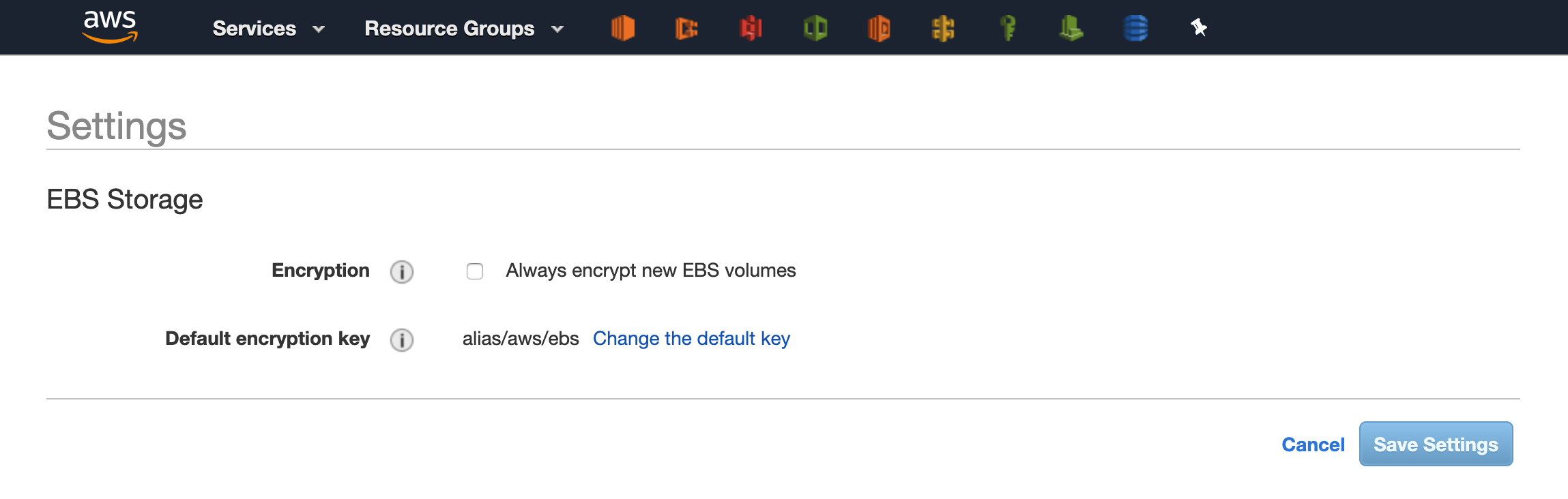
Once the settings have been saved all newly created EBS volumes in that account will be encrypted with the key chosen.
A potential gotcha
If, like many other companies, you build Amazon Machine Images (AMI) in a config or development account to share with your production account, then be cautious when using this feature. When creating a new AMI, part of the process is generating a snapshot of the volume. Whether this is a manual creation using an EC2 instance with a EBS volume attached (root or any other mounted volume) or an automated process using something like Packer (Don’t worry there will be another article on this soon).
If you have chosen the default alias/aws/ebs, then you are a little stuck, as you won’t be able to share this AMI with another account due to the permissions of that key. They will be locked down to the account of creation and no other access is allowed. So if you needing to share the AMI with another account, make sure to create your own CMK using AWS Key Management Service (KMS) and use this to encrypt the volumes. This key can then be shared to other accounts, thereby giving access to the encrypted snapshot.
Quick note: There are some other ways of doing this in a slightly better way, but its out of scope for this article, and may be covered in more depth in an upcoming article.