Failed AWS console login notifications
When it comes to securing the cloud, one often overlooked part is monitoring failed login attempts, and more specifically in this case failed login attempts to the AWS console. Of course things like strong user passwords and enabling 2FA should be the first setting you do when creating a new account. But now that you up and running, you could have a situation where someone manages to get some usernames from you company and starts trying to break in, how would you know?
AWS tools to the rescue
There are some articles out there talking about a solution that involves CloudTrail, CloutWatch Logs and a Lambda. These are valid solutions, however can be a touch expensive, especially if you have a growing cloud presence.
The solution we will be looking at makes use of CloudTrail, CloudWatch Events Rules and a SNS Topic. Sounds simple, doesn’t it? Well in the end it was, however getting to the point where I could write this article took a lot of keyboard smashing and bending the ears of some very helpful AWS Support team members.
Lets get our hands dirty
So let’s get started. As this is dealing with global logins, we need to make sure we are in the North Virginia (us-east-1) region. If you haven’t already, create a CloudTrail. Then we going to create a simple SNS Topic with your email as the subscriber. Don’t forget to confirm your email by clicking on the link in the email AWS will send. This will get the notification when the rule pattern is matched and triggers an event.
Then we go to CloudWatch and create a new Events Rule. This will look at an event source that is largely unknown “aws.signin”. This tracks every login into your account via the console, whether success or failure. We then create a rule pattern that takes that source and uses the details of eventname and reponseElements to filter the events that it reads.
Once it matches this pattern it will trigger the event and send a notification off to the SNS topic that we choose.
Rule Pattern
{
"source": [
"aws.signin"
],
"detail-type": [
"AWS Console Sign In via CloudTrail"
],
"detail": {
"eventSource": [
"signin.amazonaws.com"
],
"eventName": [
"ConsoleLogin"
],
"responseElements": {
"ConsoleLogin": [ "Failure" ]
}
}
}
Transform SNS payload
{
"username": "$.detail.userIdentity.userName",
"sourceIPAddress": "$.detail.sourceIPAddress",
"account": "$.detail.recipientAccountId",
"errorMessage": "$.detail.errorMessage"
}
"There has been a failed login attempt on account <account>, using the username <username> from <sourceIPAddress>. Error: <errorMessage>"
The new rule will look something like this:
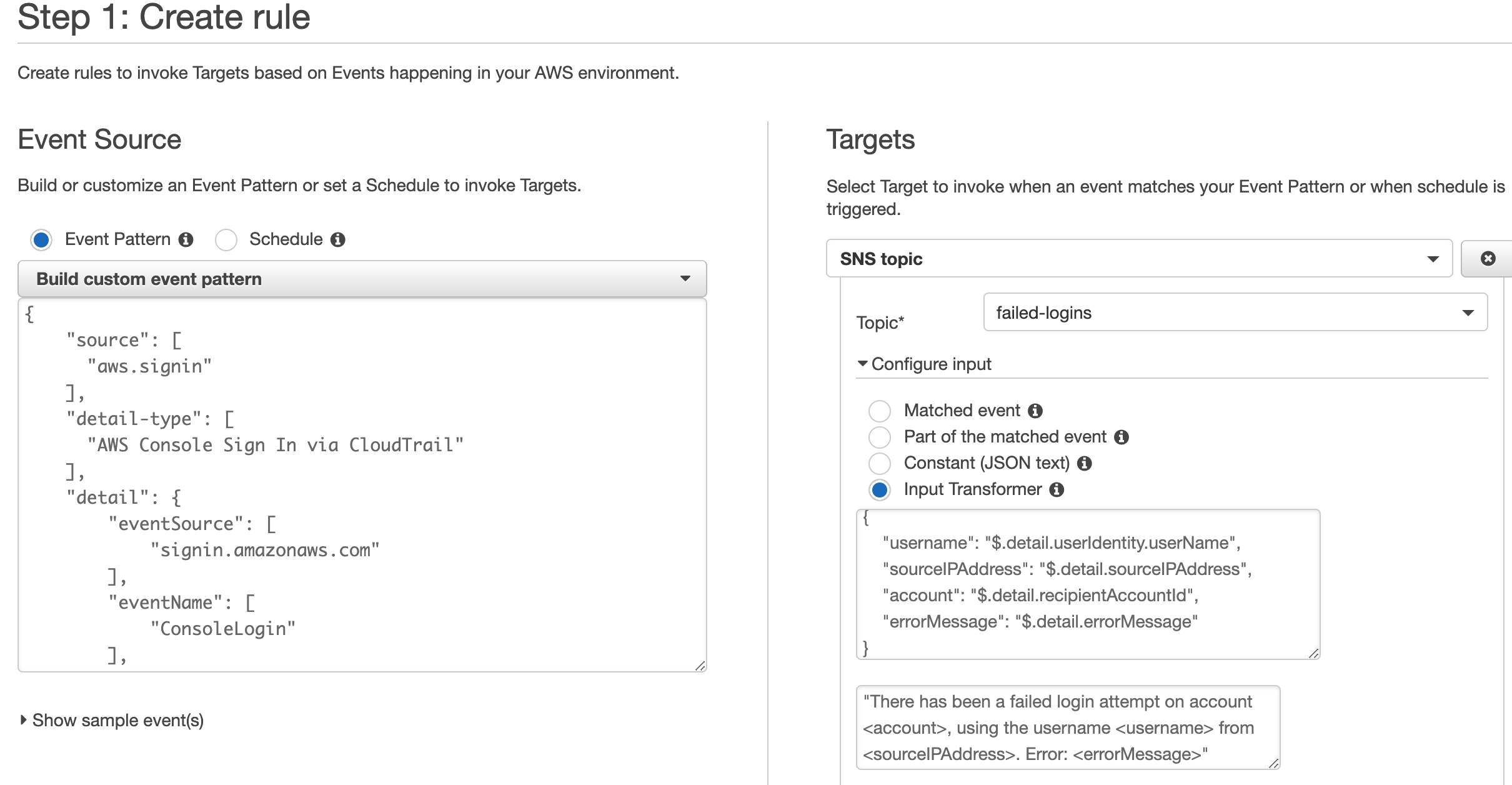
Now all that is left to do is test it. So try login to your account with an incorrect password, and then after a short wait you should receive an email in your inbox that was set in your SNS Topic.

End
So there we have it. A more simple approach to tracking failed login attempts on your AWS console. And dare I say it, much cheaper too. A big thank you needs to go our to AWS Support, as they helped me get this idea over the goal line. I knew what I wanted and was on the verge of doing it, but they were the missing piece.
I am in the process of writing the CloudFormation for this, and once done I will add it to the article. Thanks for reading and learning with me today.